SSH Raspberry Pi IoT Projects: Unlock Remote Control For Your Devices
Are you looking to take your smart home gadgets or other connected devices to the next level? Perhaps you want to keep an eye on things, or even control them, no matter where you happen to be. Well, getting your Raspberry Pi to talk securely using SSH for various IoT projects is, like, a really big deal. It opens up a whole world of possibilities for remote access and management, making your projects much more practical and safe. This approach helps ensure that only you can connect to your devices, keeping your data and systems private.
For anyone tinkering with small computers, especially the Raspberry Pi, setting up secure connections is a pretty common need. You might have a machine, say, running Ubuntu, and you want to reach it from another computer, like a Fedora setup, to run graphical programs. This kind of remote access is where SSH truly shines, offering a way to send display information back to your main computer. It's really quite handy for managing things without being right there, which is often the case with devices spread around your house or even in another building.
This guide will walk you through how SSH can become your best friend for a bunch of exciting Raspberry Pi IoT projects. We'll talk about getting started, keeping things secure with special keys, and even some cool things you can build. It's almost about making your devices truly yours, with full, safe control from anywhere. You know, it's pretty empowering.
Table of Contents
- Understanding SSH for IoT
- Setting Up SSH on Your Raspberry Pi
- Connecting Remotely and Forwarding X
- Popular SSH Raspberry Pi IoT Projects
- Troubleshooting Common SSH Issues
- Keeping Your IoT Projects Secure
- Conclusion
- Frequently Asked Questions
Understanding SSH for IoT
SSH, which stands for Secure Shell, is basically a way to connect to another computer over an unsecured network in a very safe manner. For your Raspberry Pi IoT projects, this means you can send commands, transfer files, and even run graphical applications on your Pi from another computer, all without worrying too much about someone else listening in. It's like having a direct, private line to your device, no matter if it's sitting in your living room or, say, in a remote garden shed. This is especially useful for devices that don't have a screen or keyboard attached, which is often the case with IoT gadgets.
The main idea behind using SSH for IoT is control and security. You want to be able to check on your sensors, adjust settings, or restart a service without physically going to the device. Think about a smart irrigation system; you might need to change watering times based on the weather forecast. With SSH, you can just log in from your laptop or phone and make those changes. It's a rather simple yet powerful tool, honestly.
Furthermore, SSH helps keep your projects safe from unwanted access. Instead of using easily guessed passwords, you can use something called SSH keypairs. These are much stronger and make it very difficult for anyone to break into your system. So, it's not just about convenience; it's also about protecting your smart home or other connected setups. That, you know, is pretty important these days.
Setting Up SSH on Your Raspberry Pi
Getting SSH ready on your Raspberry Pi is a straightforward process. You'll want to make sure your Pi is running properly first. This setup lets you connect to it from another computer, which is what we need for remote control. It's almost like giving your Pi a remote control button that only you can press.
Initial Setup and Enabling SSH
First things first, you need to have Raspberry Pi OS installed on your Pi. Once it's up and running, there are a few ways to enable SSH. The easiest way for many is through the Raspberry Pi Configuration tool, which you can find in the graphical desktop environment. Just go to 'Interfaces' and turn SSH 'On'.
If you're working without a screen, or just prefer the command line, you can enable SSH using `raspi-config`. Open a terminal on your Pi and type `sudo raspi-config`. Navigate to 'Interface Options' and then select 'SSH'. It will ask you if you want to enable the SSH server, and you'll choose 'Yes'. After this, your Pi should be ready to accept SSH connections. You might need to reboot, but often it works right away. This is, you know, a pretty common step for Pi users.
You'll also need to know your Raspberry Pi's IP address. You can find this by typing `hostname -I` in the Pi's terminal. Write it down, as you'll need it to connect from your other computer. This IP address is basically your Pi's address on your local network. It's a little like its phone number, you know.
Securing Your Connection with SSH Keypairs
While you can connect to SSH with a password, using SSH keypairs is a much more secure method, and it's highly recommended for IoT projects. It's a bit like having a very complex, unique digital lock and key. You keep the private key on your computer, and the public key goes on your Raspberry Pi. When you try to connect, they essentially "shake hands" to verify it's you.
To create a keypair on your computer (the one you'll be connecting from), you can use the command `ssh-keygen`. This will typically create two files: `id_rsa` (your private key) and `id_rsa.pub` (your public key). However, as a matter of fact, for specific projects, you might want to create a separate keypair, not your default `id_rsa` keypair, to keep things organized and even more secure. This is particularly true if you have, say, a dedicated SSH proxy server you need to connect to, as mentioned in my notes, using a keypair specifically for that purpose. This way, if one key is ever compromised, your other systems remain safe.
Once you have your public key, you need to copy it to your Raspberry Pi. The `ssh-copy-id` command is great for this: `ssh-copy-id pi@your_pi_ip_address`. If that doesn't work, you can manually copy the contents of your public key file (`~/.ssh/your_custom_key.pub`) and paste it into the `~/.ssh/authorized_keys` file on your Raspberry Pi. Make sure the permissions on the `authorized_keys` file are correct (`chmod 600 ~/.ssh/authorized_keys`). This step is, arguably, the most important for security.
For even better management, especially if you're using multiple keypairs, tools like `keychain` can be super helpful. You can add your identity using `keychain` to persist the key, so you don't have to enter your passphrase every time you connect. This is a tip that, apparently, many experienced users find quite useful. It makes using those special keys much less of a hassle, you know.
Connecting Remotely and Forwarding X
Once SSH is set up with your keypair, connecting to your Raspberry Pi is simple. From your computer's terminal, you just type `ssh -i ~/.ssh/your_custom_key pi@your_pi_ip_address`. The `-i` flag tells SSH to use a specific key, which is very helpful when you're not using your default key. This is, in some respects, a direct line to your Pi's command line.
Now, what if you want to run a graphical program on your Raspberry Pi but see its window on your computer? This is where X forwarding comes in. If you have, say, a machine running Ubuntu that you SSH to from your Fedora machine, and you want to forward X from the Ubuntu machine back to Fedora so you can run graphical programs remotely, SSH can do that. You simply add the `-X` flag to your SSH command: `ssh -X -i ~/.ssh/your_custom_key pi@your_pi_ip_address`. After you connect, any graphical program you launch from the Pi's command line will display on your computer's screen. It's pretty neat, honestly, for managing things like a graphical configuration tool or a simple web server interface that runs locally on the Pi.
This capability is particularly useful for IoT projects where you might need to occasionally access a visual interface without plugging in a monitor. Think about configuring a camera stream or a custom dashboard. It's almost like having a monitor built into your main computer, just for the Pi. That, you know, makes remote work much easier.
Popular SSH Raspberry Pi IoT Projects
With SSH enabled, your Raspberry Pi becomes a very versatile tool for a range of IoT projects. The ability to connect remotely and securely opens up so many possibilities. Here are just a few ideas that, basically, leverage the power of SSH.
Home Automation Hub
Turn your Raspberry Pi into the brain of your smart home. You can install home automation software like Home Assistant or OpenHAB. With SSH, you can manage and update your hub from anywhere. Imagine being able to add new smart devices, tweak automation rules, or check the status of your lights and thermostats while you're away. You can even, perhaps, use SSH to run scripts that interact with various smart devices, giving you very granular control. It's a pretty powerful way to keep your home running smoothly.
This also means you can troubleshoot issues without being home. If a sensor stops reporting, you can SSH in, check logs, or restart services. This remote access is, in fact, crucial for a reliable smart home system. It gives you peace of mind, knowing you can always connect and fix things. That, you know, is a big plus for busy people.
Remote Monitoring System
Set up your Raspberry Pi with sensors to monitor anything from temperature and humidity in your greenhouse to motion detection around your property. You can use SSH to securely retrieve data, view sensor readings, or even get real-time alerts. For example, you could have a Pi with a camera in your backyard, and SSH in to view live footage or past recordings. This is, arguably, a very practical application for many homes.
The beauty here is that the data can be stored locally on the Pi, and you can pull it down whenever you need it via SSH's secure file transfer protocol (SFTP). Or, you can just log in and run a script that displays the current readings. This makes it very flexible for various monitoring needs, like checking on a server room's temperature or a pet's activity. It's almost like having eyes and ears everywhere, you know.
Personal Cloud Storage or Server
Transform your Raspberry Pi into a personal cloud server using software like Nextcloud or OwnCloud. You can store your files, photos, and documents, accessing them securely from any device. SSH is used for the initial setup, maintenance, and for securely transferring large files to and from your cloud. This gives you full control over your data, unlike commercial cloud services.
You can also use your Pi as a small web server or a database server. For instance, if you have PostgreSQL 9.3 installed on a server running Ubuntu Server 14.04, as mentioned in my notes, and you can SSH into it via terminal to connect with `psql`, you can manage your databases remotely. While configuring a graphical tool like pgAdmin III to do the remote connection can sometimes be tricky, SSH provides a reliable command-line alternative for database administration. It's a bit like having your own mini data center, totally under your command. That, in some respects, is pretty cool.
This approach gives you a lot of flexibility for hosting small websites, personal wikis, or even a simple Git repository. When fetching or pulling from Git repositories, or cloning a repository, you might get to a point where SSH keys are needed. Using your specific SSH keypair, as discussed, ensures these operations are secure. It's a pretty robust way to manage your own digital assets, you know.
Troubleshooting Common SSH Issues
Sometimes, things don't go as planned with SSH. It's a rather common experience for anyone working with remote connections. Knowing a few basic troubleshooting steps can save you a lot of frustration. It's almost like having a little toolkit for when things get a bit bumpy.
One common issue is when your remote script returns an error, like `255`, and SSH just delivers its result to you without much explanation. This happened to me, and it can be perplexing. The best way to fix this is to, you know, actually look at the script. The remote script might have a syntax error, or it might be trying to access something that isn't there, or it might not have the right permissions to run. Showing the script, as suggested in my notes, is usually the first step to figuring out what went wrong. You might need to add `set -x` at the top of your bash script to see what commands are being executed, which can be very helpful for debugging.
Another common problem is related to SSH keys. If the documentation is not clear on how to explicitly use only a specific key, or if you're getting "Permission denied (publickey)" errors, double-check your SSH client configuration. Make sure you're using the `-i` flag with the correct path to your private key. Also, ensure the permissions on your private key file are set to `chmod 400 ~/.ssh/your_private_key`. Incorrect permissions are a very common reason for key-based authentication failures. It's a little detail that can cause big headaches, honestly.
If you're having trouble connecting to Git repositories over SSH, as mentioned, it could be due to incorrect key usage or a missing key in your SSH agent. To fix this, I simply ran a specific command (for each repo) that added the identity using `keychain`, which helps persist the key. This command, which I took from a helpful source, ensures your SSH agent knows about your key and can offer it to the Git server. It's a pretty good way to avoid repetitive key prompts. That, you know, makes life easier.
Finally, always check your network connection. Is your Raspberry Pi actually connected to the network? Can you ping its IP address? Sometimes, the simplest explanation is the right one. A quick `ifconfig` or `ip a` on the Pi can tell you if it has an IP address. It's a basic check, but, you know, often overlooked.
Keeping Your IoT Projects Secure
Security is, arguably, paramount for any IoT project, especially when you're connecting devices to the internet. SSH provides a strong foundation for secure access, but there are other steps you should take to protect your Raspberry Pi and the data it handles. It's a bit like putting multiple locks on a very important door.
First and foremost, always change the default password for the `pi` user. Better yet, create a new user account for yourself and disable the `pi` user entirely. This prevents attackers from trying common default credentials. It's a very simple step, but, you know, incredibly effective.
As we discussed, using SSH keypairs instead of passwords for authentication is a must. This is a much more robust security measure. Furthermore, make sure your private keys are stored securely on your local machine and are not accessible to others. They are, basically, the keys to your digital kingdom.
Consider setting up a firewall on your Raspberry Pi using `ufw` (Uncomplicated Firewall). This lets you control which incoming connections are allowed. For example, you can configure it to only allow SSH connections from specific IP addresses, if you have a static IP at your workplace. This is, in fact, how I manage my own setup; it is always connected and works properly when I am in the work place, so I can restrict access to just that known IP. This adds another layer of protection, preventing unauthorized access attempts. It's a pretty good way to narrow down who can even knock on your Pi's door.
Keep your Raspberry Pi OS and all installed software up to date. Regularly run `sudo apt update` and `sudo apt upgrade`. Software updates often include security patches that fix vulnerabilities. This is, truly, a continuous process for keeping your systems safe. You know, it's like regular maintenance for your car.
If you need to access your Raspberry Pi from outside your local network, avoid directly exposing SSH to the internet. Instead, consider using a VPN (Virtual Private Network) or a reverse SSH tunnel. A VPN creates a secure tunnel to your home network, allowing you to connect to your Pi as if you were on your local network. This is a much safer approach than port forwarding SSH directly through your router. This is, in some respects, a very clever way to hide your Pi from direct internet scans.
Finally, regularly review your SSH configuration file (`/etc/ssh/sshd_config`) on your Raspberry Pi. You can disable password authentication (`PasswordAuthentication no`), disable root login (`PermitRootLogin no`), and change the default SSH port from 22 to something else (though this is more of an obfuscation than a true security measure). These small tweaks can, you know, add up to a much more secure setup. Learn more about on our site.
Conclusion
Using SSH for your Raspberry Pi IoT projects truly changes how you can interact with your devices. From setting up secure remote access with unique keypairs, which is pretty important, to running graphical applications from afar, the possibilities are vast. It's about giving you control and keeping your smart gadgets safe. You can build powerful home automation systems, reliable monitoring tools, or even your own personal cloud, all managed securely. This approach helps you maintain a tight grip on your digital projects, ensuring they work properly and stay protected, no matter where you are. So, you know, it's time to start exploring what you can build. And, you might want to link to this page for even more security advice.
Frequently Asked Questions
How do I SSH into my Raspberry Pi?
You can SSH into your Raspberry Pi by first enabling SSH on the Pi itself, either through the graphical interface or using `sudo raspi-config`. Then, from your computer's terminal, you use the command `ssh pi@your_pi_ip_address`. It's pretty straightforward, honestly, once you have the Pi's IP address.
Can I use SSH for home automation?
Absolutely, you can! SSH is very useful for home automation. You can use it to remotely manage your Raspberry Pi, which can act as a home automation hub. This lets you update software, check system status, or even run scripts to control smart devices from anywhere. It's a pretty secure way to keep tabs on your smart home, you know.
What are some good IoT projects for Raspberry Pi?
There are many great IoT projects for Raspberry Pi. Some popular ones include building a home automation hub, creating a remote monitoring system for temperature or security, or setting up a personal cloud storage server. You can also make a network-wide ad blocker or a media center. The possibilities are, basically, endless, especially with SSH for remote management.
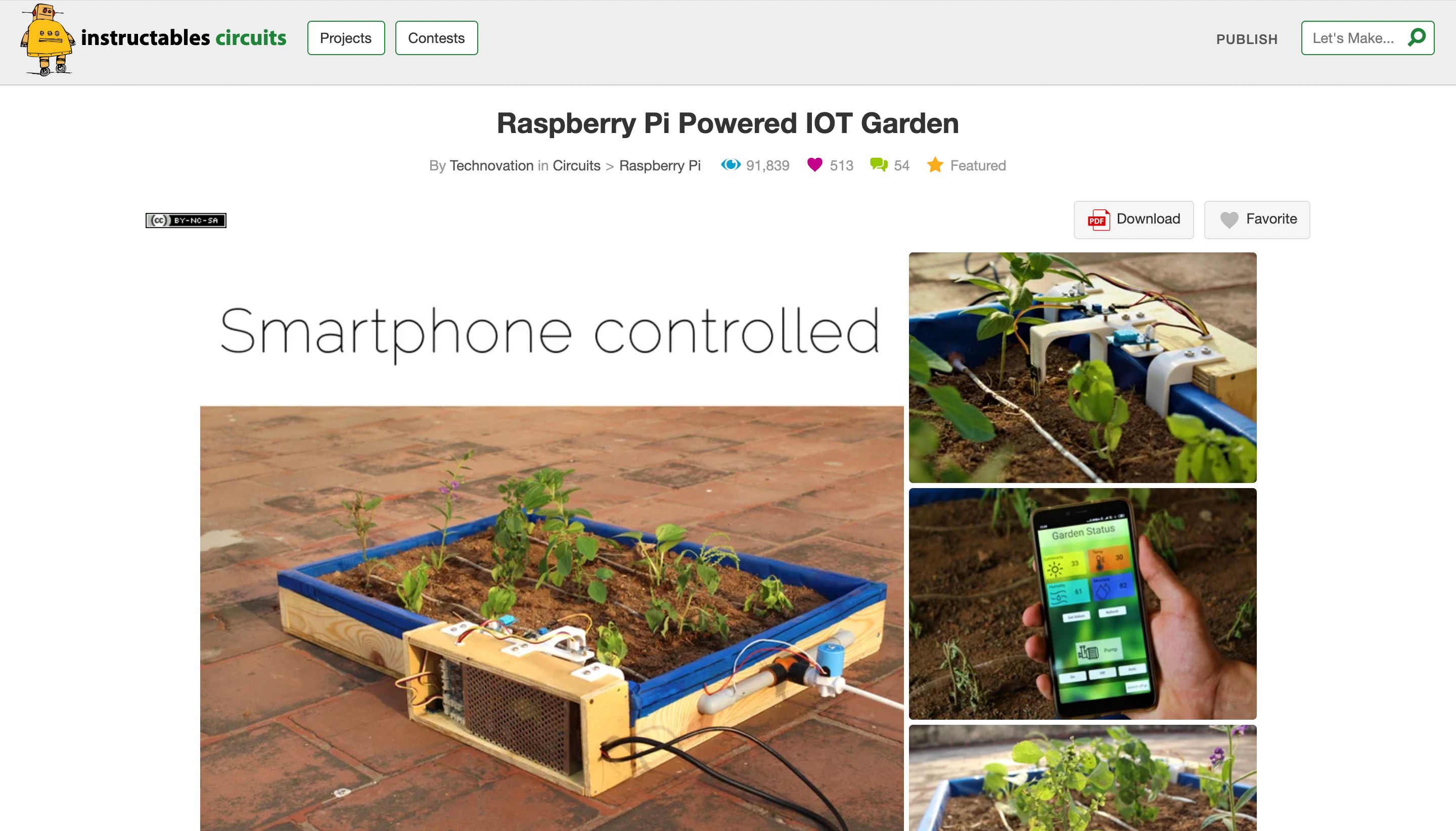
The 10 Best Raspberry Pi IoT Projects
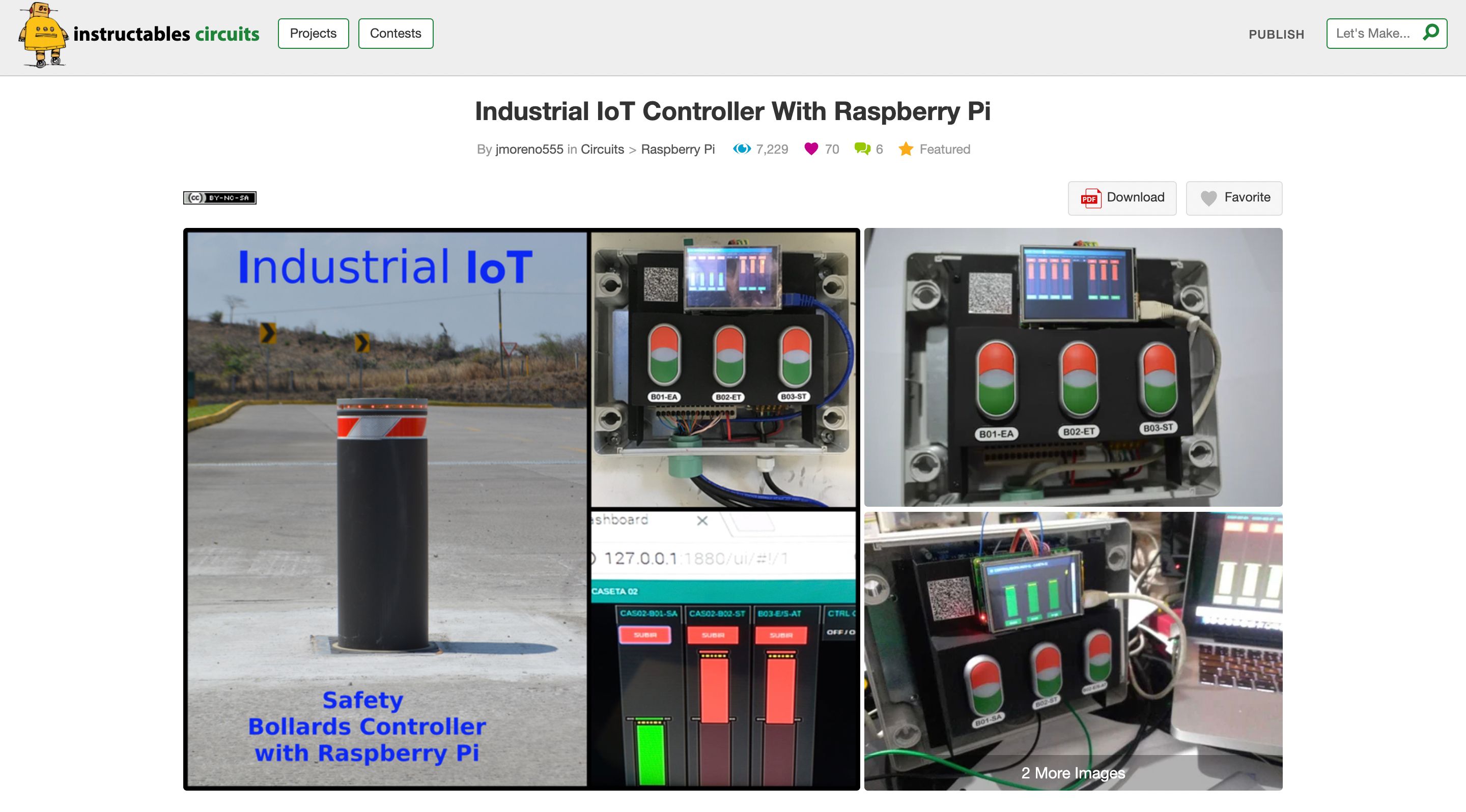
The 10 Best Raspberry Pi IoT Projects
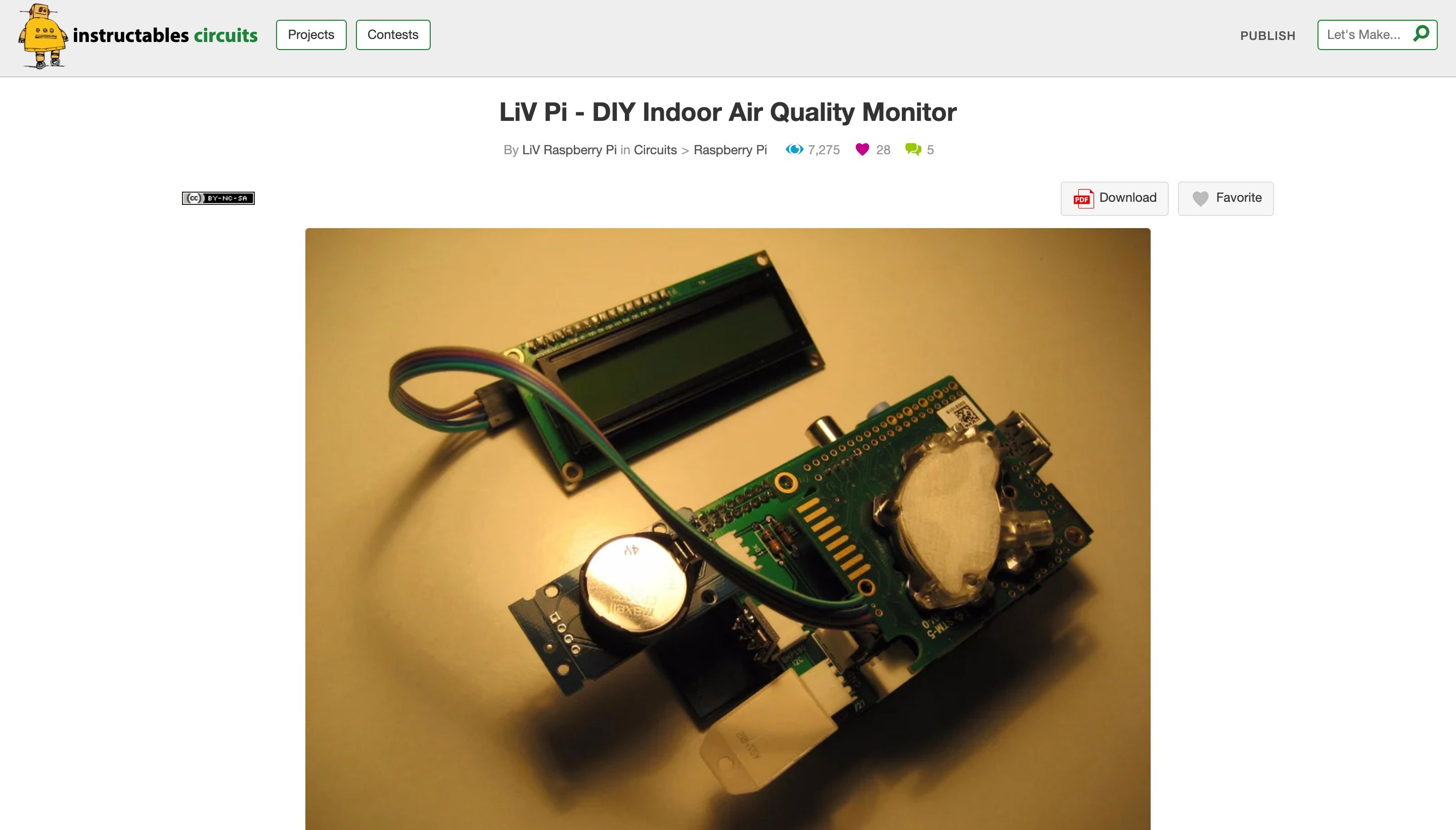
The 10 Best Raspberry Pi IoT Projects